Cracking WPA2 wifi password is not really an easy thing to do,
You can't crack it with a click and there is no software that will give you the password without some hard work ...
don't run away still you can crack it with few steps here :)
and we will do it using aircrack-ng
Requirements: To crack a wpa2-psk encrypted wifi password using aircrack-ng
1. Kali Linux or any Linux system with aircrack-ng installed
a- if you don't have aircrack-ng suite get it by this commend in terminal
2. A wireless network adapter that support monitor mode like
a- Alfa 2W AWUS036NH
b- Alfa AWUS036H
c- wifiy-city 56G
d- and you can check this page here for card compatibility compatibility drivers
3. A word list comprising of all the possible different combination of pass-phrases
Now let's get to work
1) open up your terminal as root and type
this will show you all the networking interfaces connected to your device.
if your wireless network adapter is working fine you should see the " wlan0 " the name may change if you have more then one connected wireless adapter.
2) Now to open Wifi Card in Monitoring mode
Type the command “airmon-ng” (without quotes) to see if your adapter is seen by Kali Linux.
It should show the interface, chipset, and driver.
Next type the following command to set the USB adapter into monitor mode.
'airmon-ng' is a traffic monitoring tool
‘wlan0’ is your wireless interface
3) Start Capturing Packets
Next we need to see what routers are available there and select our target so we have to do is capture the handshake with Airodump-ng. We will be using Airodump-ng first to select our target and retrieve it’s BSSID and channel the WiFi access point is broadcasting on. For this type the following command:
A complete command should look similar this:
Now you've the .cap file you'll need to decrypt it, to decrypt it open a new Terminal, and type in this command:
-a is the method aircrack will use to crack the handshake, 2=WPA method.
-b stands for bssid, replace [router bssid] with the BSSID of the target router, mine is 00:14:BF:E0:E8:D5.
-w stands for wordlist, replace [path to wordlist] with the path to a wordlist that you have downloaded. I have a wordlist called “wpa.txt” in the root folder.
/root/Desktop/*.cap is the path to the .cap file containing the password. The * means wild card in Linux, and since I’m assuming that there are no other .cap files on your Desktop, this should work fine the way it is.
so the complete command looks like this:
well now hit the enter key and you are done.
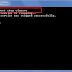
It'll start the brute force attack on the saved .cap file
and when the matched password is found its shown on the screen
So you are in the network :)
Share the Wealth
You can't crack it with a click and there is no software that will give you the password without some hard work ...
don't run away still you can crack it with few steps here :)
and we will do it using aircrack-ng
Requirements: To crack a wpa2-psk encrypted wifi password using aircrack-ng
1. Kali Linux or any Linux system with aircrack-ng installed
a- if you don't have aircrack-ng suite get it by this commend in terminal
sudo apt-get install aircrack-ng
2. A wireless network adapter that support monitor mode like
a- Alfa 2W AWUS036NH
b- Alfa AWUS036H
c- wifiy-city 56G
d- and you can check this page here for card compatibility compatibility drivers
3. A word list comprising of all the possible different combination of pass-phrases
Now let's get to work
1) open up your terminal as root and type
ifconfig
this will show you all the networking interfaces connected to your device.
if your wireless network adapter is working fine you should see the " wlan0 " the name may change if you have more then one connected wireless adapter.
2) Now to open Wifi Card in Monitoring mode
Type the command “airmon-ng” (without quotes) to see if your adapter is seen by Kali Linux.
It should show the interface, chipset, and driver.
Next type the following command to set the USB adapter into monitor mode.
airmon-ng start wlan0
'airmon-ng' is a traffic monitoring tool
‘wlan0’ is your wireless interface
3) Start Capturing Packets
Next we need to see what routers are available there and select our target so we have to do is capture the handshake with Airodump-ng. We will be using Airodump-ng first to select our target and retrieve it’s BSSID and channel the WiFi access point is broadcasting on. For this type the following command:
airodump-ng mon0
Now pick your target’s BSSID and channel and restart Airodump-ng with the following command and look for a connected client:
airodump-ng –bssid [BSSID] -c [channel]-w [filepath to store .cap]wlan0mon
A complete command should look similar this:
airodump-ng -c 10 --bssid 00:14:BF:E0:E8:D5 -w /root/Desktop/ mon0
Open a new terminal and issue an deauthentication command for the connected client using Aireplay-ng.
aireplay-ng -0 2 -a [BSSID] -c [Client MAC] mon0
aircrack-ng -a2 -b [router bssid] -w [path to wordlist] /root/Desktop/*.cap
-a is the method aircrack will use to crack the handshake, 2=WPA method.
-b stands for bssid, replace [router bssid] with the BSSID of the target router, mine is 00:14:BF:E0:E8:D5.
-w stands for wordlist, replace [path to wordlist] with the path to a wordlist that you have downloaded. I have a wordlist called “wpa.txt” in the root folder.
/root/Desktop/*.cap is the path to the .cap file containing the password. The * means wild card in Linux, and since I’m assuming that there are no other .cap files on your Desktop, this should work fine the way it is.
so the complete command looks like this:
aircrack-ng –a2 –b 00:14:BF:E0:E8:D5 –w /root/wpa.txt /root/Desktop/*.cap
It'll start the brute force attack on the saved .cap file
and when the matched password is found its shown on the screen
So you are in the network :)
Share the Wealth





0 comments